- Security Risk Assessment (Ethical Hacking) (2-2-0)
- Proactive Defence and Countermeasures (1-1-2)
- Information & network security (2-2-0)
- Cyber Hacking & Forensic Investigator (1-1-2)
- Project (0-0-4)
Cybersecurity & Digital Forensics
Domain Track : Cybersecurity & Digital Forensics
Course Attendees
Still no participant
Course Reviews
Still no reviews
Track Total Credits ( T-P-P)(6-6-8)
Courses Division( list all divisions):
Domain Track Objectives:
- This domain focusses on two aspects of Cyber Security: analysis and assessment of risk plus how to minimize it, and, how to extract and use digital information from a wide range of systems and devices.
- The domain is structured so that all students cover the same introductory material, but then choose to specialize in either Cyber Security or Digital Forensics.
- Domain is used to secure important data from enemies.
- It works as a safeguard of your computer from blackmail by the people who want to exploit the vulnerability.
- Using domain, a company or organization can find out security vulnerability and risks.
- The purpose of this domain is to evaluate the security of and identify vulnerabilities in target systems, networks or system infrastructure.
- The domain entails finding and then attempting to exploit vulnerabilities to determine whether unauthorized access or other malicious activities are possible.
Domain Learning Outcomes:
- The domain will cover basic digital forensics and network security, and also cover computer system tools and the Linux/UNIX operating system which are highly essential in the cyber world.
- Able to deal with digital evidence in a professional manner (that includes adhering to appropriate legal guidelines).
- It will then follow either the Cyber Security or Digital Forensics pathway within the course (though each leads to the same-named degree: the pathways are simply opportunities to specialize within the field).
- In addition, all students will take a Research Methods module and complete a project module to devote them to the world of research for their future edifice and expertise.
- Candidates after the completion of the domain have lucrative openings & scopes in the emerging areas surrounding research & development in academics, nuclear power plants, corporates, Govt. organization like railway, banking & also in national as well as International grounds with good designations as Chief Information Security Officer, Forensic Computer Analyst, Information Security Analyst, Digital Forensics Investigator, Digital Forensics specialist, Homeland Security Professional and many more.
Carier Prospects:
- After the completion of Cyber Security & Digital Forensics:
- Computer security practitioner
- Security auditor
- Security architect
- Network security manager
- Chief Information Security Officer
- Forensic Computer Analyst
- Information Security Analyst
- Penetration Tester
- Digital Forensics Specialist
- IT Security Engineer
- Security Systems Administrator
- Digital Forensics Investigator
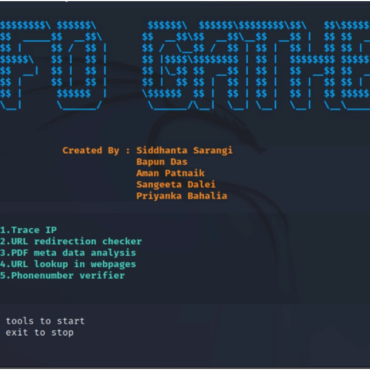
- Security Risk Assessment (Ethical Hacking)
- Information & Network Security
- Digital Forensics
- Mobile Device Forensics
- Project
Domain Syllabus:
Security Risk Assessment (Ethical Hacking) (2-2-0) (50HRs)
- Footprinting through Search Engines
- WHOIS Footprinting
- Network Footprinting
- Website Footprinting
- DNS Footprinting
- Footprinting through Social Networking
- EMAIL Footprinting
- Google Hacking
- IP Scanner
- Port Scanner
- Vulnerability Scanner
- Application Scanner
- Exploits
- Denial of Services (DoS)
- Proxy
- Is your Password Hacked?
- Password Guessing
- Browser Password Hacking
- Application Password Hacking
- OS Password Hacking
- OS Password Hacking
- Server password Hacking
- Phishing
- Sniffer
- Session Hijacking
- VIRUS
- Ransomware
- Keylogger
- Trojan/RAT
- Wireless Hacking
- Kali Linux
- Metasploit Framework
Proactive Defence and Countermeasures (1-1-2) (50HRs)
- Switch Security (Virtual LANS)
- PORT Security
- AUTO Secure
- Firewall – CISCO ASA (Initial Configuration via GUI)
- Security Policies (Default Security Policies Behaviour)
- STATIC NAT
- Redirect NAT
- DYNAMIC NAT
- PORT Address Translation
- WEB Filtering
- Authentication
- Device Authentication-Local
- Device Authentication-External
- Data Authentication-External
- Logging
- Site to site VPN (IPSEC)
- Remote Access VPN (IPSEC)
- Remote Access VPN (SSL)
- VLAN
- Trunk-VLA
- 3-INFORMATION & NETWORK SECURITY
- Overview of Information Security- Threats - Frauds, Thefts, Malicious Hackers, Malicious Code, Denial-of-Services Attacks and Social Engineering, Vulnerability–Types Database Security-Overview of Database - Database application security models-Data base auditing models-Application data auditing-Practices of database auditing. Data Loss prevention – Content Filtering - Device Control - Network DLP - Host DLP. Network Security & Web Security: Security Issues in TCP/IP – TCP, DNS, Routing (Topics such as basic problems of security in TCP/IP, IPsec, BGP Security, DNS Cache poisoning etc.), Network Défense tools – Firewalls, Intrusion Detection, Filtering, Distributed Firewalls, Security architecture of World Wide Web, Security Architecture of Web Servers, and Web Clients, Web Application Security –Cross-Site Scripting Attacks, Cross-Site Request Forgery, Https, Threat Modelling, Attack Surfaces.
- Configuring Window Firewall.
- Configuring Linux Firewall.
- Adding users,setting permissions in windows.
- Port Security.
- Access control List in Linux.
- Nmap scanning tool using both Linux and Windows.
- Installing and configuration of Linux firewall iptables.
- Study various methods for taping into wire.
- Study the steps for installing Wireshark, the packet sniffing tool for performing Network Analysis.
- Study of working with captured packets.
- Study of advanced Wireshark features.
- Study of security packet analysis.
Cyber Forensics (1-1-2) (50HRs)
- Computer Forensics Investigation Process.
- Recovering Deleted Files from the evidence.
- Generating Hashes & Checksum Files.
- Calculating the MD5 value of the selected File.
- Viewing Files of Various Formats.
- Handling Evidence Data.
- Creating a Disk Image File of an HDD Partition.
- Understanding HDD & its File Systems.
- Recovering Deleted Files from Hard Disks Using WINHEX.
- Analysing File System Types Using the Sleuth Kit.
- Analyzing Raw Image Using Autopsy.
- Data Acquisition & Duplication.
- Investigating NTFS Drive Using DiskExplorer for NTFS.
- Viewing Content of Forensic Image Using AccessData FTK Imager Tool.
- Discovering & Extracting Hidden Forensic Material on Computers using Computer Forensics.
- Extracting Information about Loaded Processes Using Process Explorer.
- The viewing, Monitoring, and Analysing Events using the Event Log Explorer Tool.
- Performing Computer Forensic Investigation using the Helix Tool.
- Using Volatile Data in Linux System.
- Analyzing Non-Volatile Data in Linux System.
- Capturing and Analysing Logs of Computer using GFI Events Manager.
- Investigating System Log Data Using Xpolog Center Suite.
- Investigating Network Attacks using Kiwi Log Viewer.
- Investigating Network traffic using Wireshark.
- Investigating Web Attacks (Analysing Domain & IP Address Queries Using SmartWhois Tool.
Project (0-0-4) (Major)
- Project from the field of Cybersecurity.
- Live Setup and configuration using core tools and techniques.
- Project from the field of Digital Forensics.
- Live investigation Acquisition, analysis, and reporting using forensic tools and techniques.
Session Plan for the Entire Domain:
Security Risk Assessment (Ethical Hacking) (2-2-0) (50HRs)
Session 1 to 4
- Footprinting through Search Engines
- WHOIS Footprinting
- Network Footprinting
Session 5 to 13
- Website Footprinting
- DNS Footprinting
- Footprinting through Social Networking
- EMAIL Footprinting
Session 14 to 16
- Google Hacking
- IP Scanner
Session 17 to 19
- Port Scanner
- Vulnerability Scanner
Session 20 to 23
- Web Application Scanner
- Exploits
Session 24 to 26
- Denial of Services (DoS)
Session 27 to 30
- Proxy
Session 31 to 32
- Is your Password Hacked?
- Password Guessing
Session 33 to 34
- Browser Password Hacking
- Application Password Hacking
Session 35 to 37
- OS Password Hacking
- OS Password Hacking
Session 38 to 39
- Server password Hacking
- Cisco Password Hacking
Session 40 to 42
- Phishing
- Sniffer
- Session Hijacking
Session 43 to 45
- VIRUS
- Ransomware
- Keylogger
Session 46 to 47
- Trojan/RAT
- Wireless Hacking
Session 48 to 50
- Kali Linux
- Metasploit Framework
Proactive Defence and Countermeasures (1-1-2) (50HRs)
Session 1 to 3
- Switch Security (Virtual LANS)
Session 4 to 7
- PORT Security
Session 8 to 10
- AUTO Secure
Session 11 to 14
- Firewall – CISCO ASA (Initial Configuration via GUI)
Session 15 to 18
- Security Policies (Default Security Policies Behaviour)
Session 19 to 22
- STATIC NAT
Session 23 to 26
- Redirect NAT
Session 27 to 29
- DYNAMIC NAT
Session 30 to 32
- PORT Address Translation
Session 33 to 35
- WEB Filtering
Session 36 to 39
- Authentication
- Device Authentication-Local
- Device Authentication-External
- Data Authentication-External
Session 40 to 44
- Logging
- Site to site VPN (IPSEC)
- Remote Access VPN (IPSEC)
Session 45 to 50
- Remote Access VPN (SSL)
- VLAN
- Trunk-VLAN
Incident Response and Management (2-2-0) (50HRs)
Session 1 to 2
- Security Information and Event Management (SIEM)
Session 3 to 4
- Installing of OSSIEM
Session 5 to 6
- Configuring OSSIM
Session 7 to 8
- Forwarding DHCP Server Logs to OSSIM
Session 9 to 10
- Install NXLog on Windows Server
Session 11 to 12
- Configure NXLog on Windows Server to Forward Logs to OSSIM
Session 13 to 14
- Configure OSSIM for processing DHCP Server logs
Session 15 to 16
- Verify DHCP Server in OSSIM
Session 17 to 18
- Configure Alarm for selected DHCP Server Events
Session 19 to 20
- Verify Alarm in OSSIM
Session 21 to 22
- Forwarding DNS Server logs to OSSIM
Session 23 to 24
- Instal NXLog on Windows Server to forward logs to OSSIM
Session 25 to 26
- Verify DNS Server Events in OSSIM
Session 27 to 28
- Forwarding ASA Firewall to forward logs to OSSIM
Session 29 to 30
- Configure OSSIM for processing ASA Firewall logs
Session 31 to 32
- Verify ASA Firewall Events in OSSIM
Session 33 to 34
- Configure Alarm foe selected ASA Firewall Events
Session 35 to 36
- Verify Alarm in OSSIM
Session 37 to 38
- Forwarding Security Events to OSSIM through HIDS Agent
Session 39 to 40
- Deploying HIDS Agent
Session 41 to 42
- Configuring HIDS Agent for USB Monitoring
Session 43 to 44
- Verify USB Monitoring Events in OSSIM
- Configure OSSIM for the File Integrity Monitoring
Session 45 to 50
- Verify File Integrity Monitoring Events in OSSIM
- Checking for Rootkit and Malicious Application via OSSIM
- Verify Rootkit and Malicious Application detection in OSSIM
- Cyber Forensics (1-1-2) (50HRs)
Session 1 to 2
- Computer Forensics Investigation Process.
Session 3 to 4
- Recovering Deleted Files from the evidence.
Session 5 to 6
- Generating Hashes & Checksum Files.
Session 7 to 8
- Calculating the MD5 value of the selected File.
Session 9 to 10
- Viewing Files of Various Formats.
Session 11 to 12
- Handling Evidence Data.
Session 13 to 14
- Creating a Disk Image File of an HDD Partition.
Session 15 to 16
- Understanding HDD & its File Systems.
Session 17 to 18
- Recovering Deleted Files from Hard Disks Using WINHEX.
Session 19 to 20
- Analysing File System Types Using the Sleuth Kit.
Session 21 to 22
- Analysing Raw Image Using Autopsy.
Session 23 to 24
- Data Acquisition & Duplication.
Session 25 to 26
- Investigating NTFS Drive Using DiskExplorer for NTFS.
Session 27 to 28
- Viewing Content of Forensic Image Using AccessData FTK Imager Tool.
Session 29 to 30
- Discovering & Extracting Hidden Forensic Material on Computers using Computer Forensics.
Session 31 to 32
- Extracting Information about Loaded Processes Using Process Explorer.
Session 33 to 34
- Viewing, Monitoring and Analysing Events using the Event Log Explorer Tool.
Session 36 to 37
- Performing Computer Forensic Investigation using the Helix Tool.
Session 38 to 39
- Using Volatile Data in Linux System.
Session 40
- Analysing Non-Volatile Data in Linux System.
Session 41 to 43
- Capturing and Analysing Logs of Computer using GFI Events Manager.
- Investigating System Log Data Using Xpolog Center Suite.
Session 44 to 46
- Investigating Network Attacks using Kiwi Log Viewer.
- Investigating Network traffic using Wireshark.
- Investigating Web Attacks (Analysing Domain & IP Address Queries Using SmartWhois Tool.
List of Projects to be done in domain:
Project (0-0-4) (Major)
Live Setup and configuration using core tools and techniques:
- Security Risk & Ethical Assessment.
- Proactive Defence and Countermeasures.
- Incident Response and Management.
- Cyber Hacking & Forensic Investigator (Live investigation Acquisition, analysis and reporting using forensic tools and techniques).
Student Projects:
Media