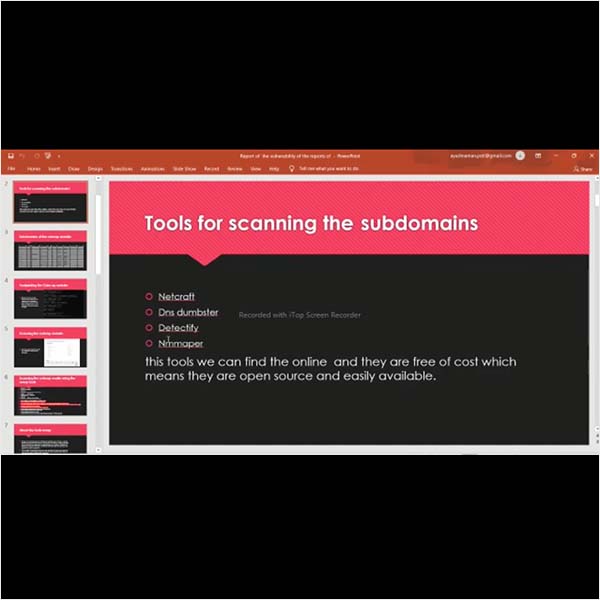
Cyber security is the practice of protecting computers, servers, mobile devices, critical electronic systems, networks, and data from malicious digital attacks.Cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.
This course gives students an insight into the basics of cloud computing along with virtualization, cloud computing is one of the fastest growing domain from a while now. It will provide the students basic understanding about cloud and virtualization along with it how one can migrate over it.